
Posts Tagged Adoption
Menu for .UA DNSSEC deployment
Posted by Mark Feldman in Uncategorized on March 19, 2012
At ICANN43, Steve Crocker, ICANN Board Chairman and DNSSEC Deployment Initiative memember, met with Dmitry Kohmanyuk, the .UA hostmaster. On the back of a menu for the Gala Dinner, Dmitry outlined the plans for .UA DNSSEC deployment.
Crocker notes
This makes the set of DNSSEC deployment maps I presented on the 14th obsolete, and I’m very happy about that.
Planned .UA DNSSEC a of 14 March 2012
(As with other menus, substitutions may occur)
- Experimental: 1 March 2012
- Announcement: 3 December 2011
- Partial Operation: 1 April 2012
- DS in Root: 15 April 2012
- Full Operation: 1 December 2012
DNSSEC in ccTLDs, Past, Present, and Future
Posted by Mark Feldman in Uncategorized on March 12, 2012
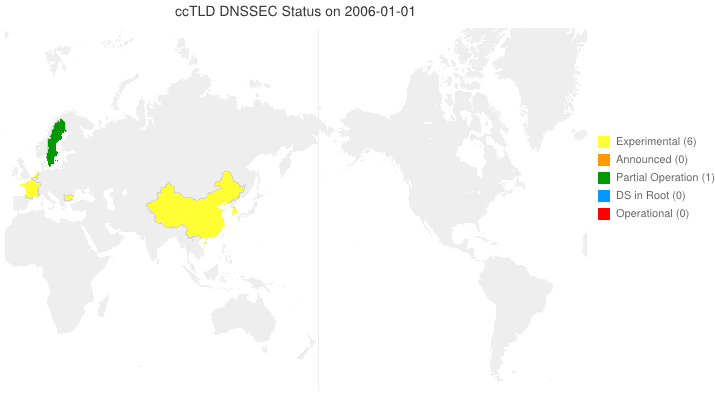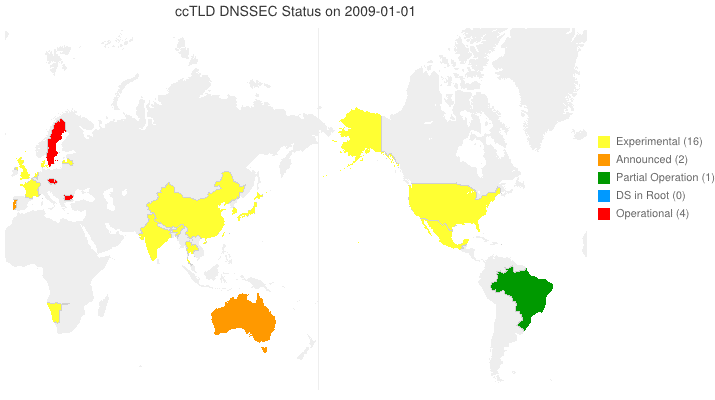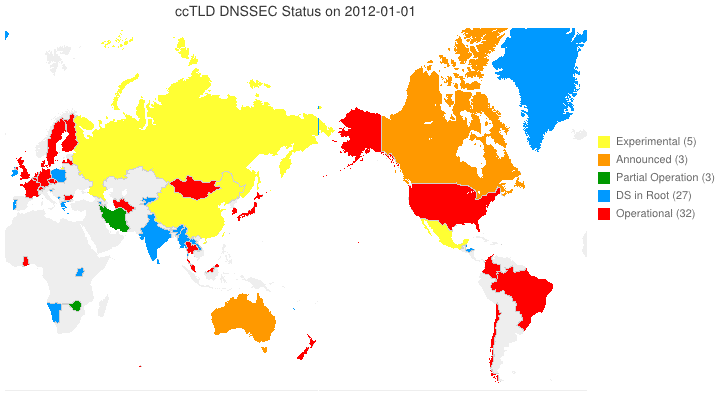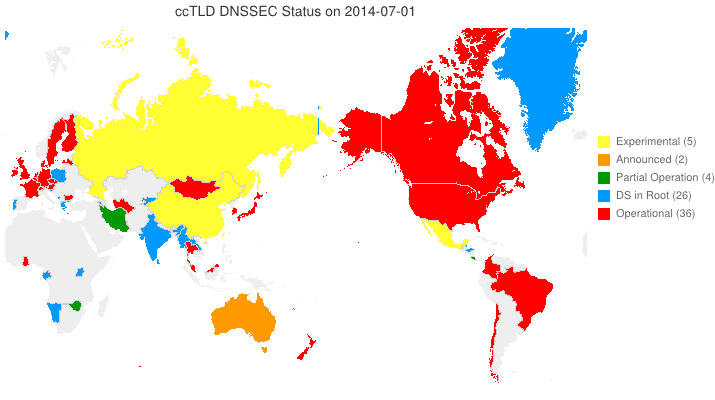
This animated GIF shows announced, estimated, and actual DNSSEC adoption by ccTLDs from January 2006 through July 2014 as of March 6, 2012. The map is a work in progress. We’re pretty sure about the past and present. If you manage a ccTLD and have a schedule for deployment or have updates/corrections, let us know at info @ dnssec-deployment.org. We’d like to see a more colorful, even completely red, map in the future.
Key:
- Experimental: We have reason to believe the ccTLD is experimenting with DNSSEC.
- Announced: The ccTLD has announced that they will support DNSSEC.
- Partial Operation: The ccTLD is signed, though possibly doesn’t have its DS in the root or isn’t taking signed delegations.
- DS in Root: The ccTLD has placed its DS in the root.
- Operational : The ccTLD is signed, its DS is in the root, and it is taking signed delegations.
DNSSEC in Higher Education — 1% isn’t enough
Posted by Mark Feldman in Uncategorized on March 7, 2012
Institutions of higher education throughout the world have been key advocates of Internet technologies. The .EDU gTLD is signed, however, a recent survey of .EDU names shows that only about one percent are signed. While this is a greater than the Internet as a whole, it is far less than TLDs that are requiring or otherwise strongly advocating DNSSEC.
On the pedestrian side, colleges and universities present a microcosm of the Internet as a whole, replete with cyber attacks, some of which could prevented by a combination of DNSSEC signing and validation. On the academic side, DNSSEC adds to the authenticity of the academic work product.
If you teach at, work at, attend, or attended any of the following, congratulations — your school is signed:
| acadiana.edu | baker.edu | berkeley.edu |
| bucknell.edu | carnegiemellon.edu | cltc.edu |
| cmu.edu | coloradomesa.edu | csupomona.edu |
| cuhk.edu | desales.edu | fhsu.edu |
| fhtc.edu | gtc.edu | hfg.edu |
| highlands.edu | indiana.edu | indianatech.edu |
| internet2.edu | iu.edu | iub.edu |
| iupui.edu | jhuapl.edu | kestrel.edu |
| lctcs.edu | lsu.edu | ltc.edu |
| ma.edu | mesa.edu | mesastate.edu |
| millikin.edu | minnesota.edu | monmouth.edu |
| mst.edu | myneltc.edu | nau.edu |
| northcentral.edu | northshorecollege.edu | nwltc.edu |
| oxford-university.edu | pacificu.edu | penn.edu |
| psc.edu | richland.edu | rockefeller.edu |
| scl.edu | sdsmt.edu | southern.edu |
| suu.edu | tilburguniversity.edu | tiss.edu |
| truman.edu | ualr.edu | ucaid.edu |
| ucb.edu | ucberkeley.edu | uccv.edu |
| ucr.edu | uiowa.edu | umbc.edu |
| uni-stuttgart.edu | upenn.edu | upf.edu |
| valencia.edu | washjeff.edu | weber.edu |
We’re sorry if your school is signed and we missed it. Our survey was limited to the .EDU gTLD. We know that many schools outside of the US are under their countries’ academic second-level domains or directly under their countries’ ccTLDs. If your school isn’t signed, DNSSEC resources tailored to Higher Education are published by:
- EDUCAUSE, the nonprofit association whose mission is to advance higher education by promoting the intelligent use of information technology, manages the .EDU TLD and worked to get it signed. They have a collection of resources for their members and others throughout the Internet.
- Internet2, the advanced networking consortium led by the U.S. research and education community, is also supporting DNSSEC within its membership. They have a DNS SIG.
The DNSSEC Deployment Initiative is ready to help. Contact us at info @ dnssec-deployment.org to discuss DNSSEC presentations for conferences and meetings.
APNIC starts third phase of DNSSEC deployment
Posted by Denise Graveline in Uncategorized on June 11, 2010
APNIC, which provides Internet addressing services to the Asia Pacific region, is now in phase three of its DNSSEC deployment, in which it will introduce its members’ DNSSEC data. In previous phases, the group conducted a DNSSEC platform test and signed its zones. In the new phase, the announcment notes, members can “enable DNSSEC protection to their reverse zones by registering Delegation Signer (DS) resource records to their parent zone data that is stored in APNIC’s name servers. The phase 3 addition to MyAPNIC’s reverse delegation screen is an optional field that allows Members to enter the DS record when they are ready to implement DNSSEC.”
DNSSEC deployed in .US; .BIZ shortly to follow, Neustar says
Posted by Denise Graveline in Uncategorized on June 7, 2010
Neustar announced today that DNSSEC has been deployed in the .US zone, and says that it is ready to accept Delegation Signer records. The .BIZ zone will be signed next, with DS record accepted as early as July 15, 2010. As a result, it will be “the second gTLD to be fully DNSSEC-enabled.”
Update – The .BIZ domain was signed on August 7, 2010.
ICANN Nairobi DNSSEC workshop now available online
Posted by Denise Graveline in Uncategorized on March 10, 2010
Today’s DNSSEC Workshop at the ICANN Nairobi meeting is now available online, with presentations and transcripts. The meeting also included live options for remote participants, which are now closed.
Comcast to deploy DNSSEC by 1st quarter 2011
Posted by Denise Graveline in Uncategorized on February 23, 2010
After two years of testing DNSSEC, Comcast — the largest provider of cable services in the U.S., with 23.6 million cable customers, 15.9 million high-speed Internet customers and 7.6 million voice customers — announced it is starting a trial today and plans to implement DNSSEC by the first quarter of 2011 or sooner. In a blog post, Comcast noted:
We plan to implement DNSSEC for the websites we manage, such as comcast.com, comcast.net and xfinity.com, by the first quarter of 2011, if not sooner. By the end of 2011, we plan to implement DNSSEC validation for all of our customers….If you don’t want to wait until 2011, you can participate in our DNSSEC customer trial, which starts today. Opt-in by changing your DNS server IP addresses to 75.75.75.75 and 75.75.76.76 (we’ll be adding IPv6 addresses soon). The servers supporting this are deployed nationally in the same locations as our other DNS servers that millions of customers use everyday.
You can find FAQs on the Comcast trial here.
Free registration available for FOSE, DNSSEC session
Posted by Denise Graveline in Uncategorized on February 14, 2010
 FOSE, the federal information technology conference and expo, offers free registration to federal employees and military personnel. Don’t fit into those categories? The DNSSEC Deployment Coordination Initiative can offer you free registration at this special link.
FOSE, the federal information technology conference and expo, offers free registration to federal employees and military personnel. Don’t fit into those categories? The DNSSEC Deployment Coordination Initiative can offer you free registration at this special link.
You can see the full program for the March 24 daylong session “What’s Next in DNSSEC,” sponsored by the Initiative, here. Featured will be updates on U.S. federal government DNSSEC deployment and next steps; state, municipal and public-private network deployment; perspectives on DNSSEC in the commercial, educational and nonprofit sector domains; and lessons learned from deployment across the federal system. The program is free but requires pre-registration.
Deployment watch: Nominet to sign .UK March 1
Posted by Denise Graveline in Uncategorized on January 28, 2010
Nominet, the Internet registry for .UK domain names, has announced it will implement DNSSEC in zones it manages, beginning March 1, 2010 with the .UK top-level domain. The announcement notes:
With the signing of the root so close (scheduled for mid-2010), we have taken the decision not to include the keys in the major DNSSEC key stores…Instead, we will use the period as an extended operational test, waiting until the root goes live before publishing our trust anchor in the root zone.
The next phase will include signing .co.uk and other SLDs, Nominet said.
Infoworld report on Africa and DNSSEC
Posted by Denise Graveline in Adoption on January 11, 2010
Infoworld reports in an article this week that “Africa’s Top Level Domain registries have opted for a slow adoption of Domain Name System Security Extensions, hoping to learn lessons from countries that pioneered the process.” The article notes that DNSSEC training is planned for African TLDs during the ICANN meeting in Nairobi in March, and quotes the Internet Society’s Michuki Mwangi, a former president of AfTLD: “Africa has an advantage in terms of management of domains because they are few compared to other countries; it may be an opportunity for Africa’s budding e-commerce to take off on a fully secure environment.”



Recent Comments