
Archive for category Uncategorized
Call for Participation — ICANN DNSSEC and Security Workshop at ICANN68 Virtual Policy Forum in June 2020
Posted by Dan York in Uncategorized on May 11, 2020
If you are interested in speaking at the ICANN 68 DNSSEC Workshop, please send a brief (1-2 sentence) description of your proposed presentation to [email protected] by 29 May 2020. This online workshop will be Monday, 22 June 2020, from 02:00 – 04:30 UTC (10:00 – 12:30 Kuala Lumpur)
****We are doing something new this time and would like to get a feel for attendance for this virtual meeting. Please RSVP here: https://forms.gle/XSH7ZhZWrViDimNN9*****
CALL FOR PARTICIPATION
The DNSSEC Deployment Initiative and the Internet Society Deploy360 Programme, in cooperation with the ICANN Security and Stability Advisory Committee (SSAC), are planning a DNSSEC and Security Workshop for the ICANN68 Virtual Policy Forum being held from 22-25 June 2020.
This workshop will be held on Monday 22, June 2020 10:00 – 12:30 Kuala Lumpur (02:00 – 04:30 UTC).
The DNSSEC and Security Workshop has been a part of ICANN meetings for several years and has provided a forum for both experienced and new people to meet, present and discuss current and future DNSSEC deployments. For reference, the most recent session was held at the ICANN67 Virtual Meeting on 11 March 2020. The presentations and transcripts are available at: https://67.schedule.icann.org/meetings/1152570
The DNSSEC Workshop Program Committee is developing a 3-hour program. Proposals will be considered for the following topic areas and included if space permits. In addition, we welcome suggestions for additional topics either for inclusion in the ICANN68 workshop, or for consideration for future workshops.
1. Global DNSSEC Activities Panel
For this panel, we are seeking participation from those who have been involved in DNSSEC deployment as well as from those who have not deployed DNSSEC but who have a keen interest in the challenges and benefits of deployment, including Root Key Signing Key (KSK) Rollover activities and plans.
2. DNSSEC Best Practice
Now that DNSSEC has become an operational norm for many registries, registrars, and ISPs, what have we learned about how we manage DNSSEC? Do you still submit/accept DS records with Digest Type 1? What is the best practice around key roll-overs? What about Algorithm roll-overs? Do you use and support DNSKEY Algorithms 13-16? How often do you review your disaster recovery procedures? Is there operational familiarity within your customer support teams? What operational statistics have we gathered about DNSSEC? Are there experiences being documented in the form of best practices, or something similar, for transfer of signed zones? Activities and issues related to DNSSEC in the DNS Root Zone are also desired.
3. DNSSEC Deployment Challenges
The program committee is seeking input from those that are interested in implementation of DNSSEC but have general or particular concerns with DNSSEC. In particular, we are seeking input from individuals that would be willing to participate in a panel that would discuss questions of the following nature:
- Are there any policies directly or indirectly impeding your DNSSEC deployment? (RRR model, CDS/CDNSKEY automation)
- What are your most significant concerns with DNSSEC, e.g., complexity, training, implementation, operation or something else?
- What do you expect DNSSEC to do for you and what doesn’t it do?
- What do you see as the most important trade-offs with respect to doing or not doing DNSSEC?
4. Security Panel
The program committee is looking for presentations on DNS and Routing topics that could impact the security and/or stability of the Internet:
- DoH and DoT implementation issues, challenges and opportunities
- RPKI adoption and implementation issues, challenges and opportunities
- BGP/routing/hijack issues, challenges and opportunities
- MANRS implementation challenges and opportunities
- Emerging threats that could impact (real or perceived) the security and/or stability of the Internet
- Domain hacking/hijacking prevention, best practice and techniques
- Browser related security implementations
- DMARC Challenges, opportunities and Best Practices
- BGP Flowspec challenges, opportunities and Best Practices
If you are interested in participating, please send a brief (1-2 sentence) description of your proposed presentation to
[email protected]
by 29 May 2020.
****We are doing something new this time and would like to get a feel for attendance for this virtual meeting. Please RSVP here: https://forms.gle/XSH7ZhZWrViDimNN9*****
Thank you,
Kathy and Andrew
On behalf of the DNSSEC Workshop Program Committee:
Mark Elkins, DNS/ZACR
Jacques Latour, .CA
Russ Mundy, Parsons
Ondrej Filip, CZ.NIC
Yoshiro Yoneya, JPRS
Fred Baker, ISC
Dan York, Internet Society
Call for Participation — ICANN DNSSEC and Security Workshop at ICANN67 in March 2020 in Cancun, Mexico
Posted by Dan York in Uncategorized on January 28, 2020
The ICANN Security and Stability Advisory Committee (SSAC) and the Internet Society Deploy360 Programme are planning a DNSSEC and Security Workshop during the ICANN67 meeting held from 07-12 March 2020 in Cancun, Mexico.
The original DNSSEC Workshop has been a part of ICANN meetings for many years and has provided a forum for both experienced and new people to meet, present and discuss current and future DNSSEC deployments. The program committee added a new focus on security to the workshop to address various emerging security related issues such as DoT/DoH impacts and potential abuses, impacts of RPKI deployments, BGP hijacking and other Internet related routing issues.
For reference, the most recent session was held at the ICANN Annual General Meeting in Montreal, Quebec on 06 November 2019. The presentations and transcripts are available at: https://66.schedule.icann.org/meetings/1116787 and https://66.schedule.icann.org/meetings/1116788
The DNSSEC and Security Workshop Program Committee is developing a 3-hour program. Proposals are sought for the following topic areas:
1. Global DNSSEC Activities Panel
For this panel, we are seeking participation from those who have been involved in DNSSEC deployment as well as from those who have not deployed DNSSEC but who have a keen interest in the challenges and benefits of deployment, including Root Key Signing Key (KSK) Rollover activities and plans.
2. DNSSEC Best Practice
Now that DNSSEC has become an operational norm for many registries, registrars, and ISPs, what have we learned about how we manage DNSSEC? Do you still submit/accept DS records with Digest Type 1? What is the best practice around key roll-overs? What about Algorithm roll-overs? Do you use and support DNSKEY Algorithms 13-16? How often do you review your disaster recovery procedures? Is there operational familiarity within your customer support teams? What operational statistics have we gathered about DNSSEC? Are there experiences being documented in the form of best practices, or something similar, for transfer of signed zones? Activities and issues related to DNSSEC in the DNS Root Zone are also desired.
3. DNSSEC Deployment Challenges
The program committee is seeking input from those that are interested in implementation of DNSSEC but have general or particular concerns with DNSSEC. In particular, we are seeking input from individuals that would be willing to participate in a panel that would discuss questions of the following nature:
- Are there any policies directly or indirectly impeding your DNSSEC deployment? (RRR model, CDS/CDNSKEY automation)
- What are your most significant concerns with DNSSEC, e.g., complexity, training, implementation, operation or something else?
- What do you expect DNSSEC to do for you and what doesn’t it do?
- What do you see as the most important trade-offs with respect to doing or not doing DNSSEC?
4. Security Panel
New to recent workshops, the program committee is looking for presentations on DNS and Routing topics that could impact the security and/or stability of the Internet.
- DoH and DoT issues, challenges and opportunities including misuse of the technologies (such as distribution of malware via DoH)
- RPKI adoption and implementation issues, challenges and opportunities
- BGP/routing/hijack issues, challenges and opportunities
- MANRS implementation challenges and opportunities
- Do multiple security mechanisms dilute the need for each of the mechanisms (e.g. DNSSEC, DoH and DoT)
- Emerging threats that could impact (real or perceived) the security and/or stability of the internet
- Domain hacking/hijacking prevention, best practice and techniques
- Browser related security implementations
- DMARC Challenges, opportunities and Best Practices
- BGP Flowspec challenges, opportunities and Best Practices
In addition, we welcome suggestions for additional topics, either for inclusion in the ICANN67 workshop, or for consideration for future workshops.
If you are interested in participating, please send a brief (1-2 sentence) description of your proposed presentation to [email protected] by 07 February 2020.
Thank you,
Andrew and Kathy
On behalf of the DNSSEC and Security Workshop Program Committee:
Mark Elkins, DNS/ZACR
Jacques Latour, .CA
Russ Mundy, Parsons
Ondrej Filip, CZ.NIC
Yoshiro Yoneya, JPRS
Fred Baker, ISC
Dan York, Internet Society
Slides and video available for ICANN 66 DNSSEC Workshop
Posted by Dan York in Uncategorized on November 18, 2019
The slides and video recording of the DNSSEC Workshop held at the ICANN 66 meeting on November 6, 2019, can now be found at these two links:
The full agenda for the session was:
- 1330-1345 – Presentation: Dan York, ISOC — DNSSEC Workshop Introduction, Program, Deployment Around the World – Counts, Counts, Counts
- 1345-1405 – Daniel Migault, Ericsson and Dan York, ISOC – Internet Draft: Best Practices for DNSSECValidating Resolvers
- 1405-1425 – Russ Mundy, Parsons – RPKI Introduction
- 1425-1445 – Update on the next KSK Roll – Kim Davies, ICANN
- 14:45-15:00 – Yoshiro Yoneya, JRPS – Towards Detecting DNNSEC validation failure with passive measurements at TLD DNS Servers
- 1515-1535 – Jaap Akkerhuis , NLnet Labs – Routing Security
- 1535-1555 – Dan York, ISOC – MANRS Observatory
- 1555-1615 – Marc Van Wesemael, EURid and Lieven Desemt, KU Leuven – Detection and prevention of domain name abuse in .eu.
1615-1645 – Workshop Summary
The next DNSSEC Workshop will be held at ICANN 67 in Cancún in March 2020. Watch for the Call for Presentations coming soon!
Call for Participation – ICANN DNSSEC and Security Workshop at ICANN66, Montreal, Canada
Posted by Dan York in Uncategorized on September 24, 2019
The ICANN Security and Stability Advisory Committee (SSAC) and the Internet Society Deploy360 Programme are planning a DNSSEC and Security Workshop on Wednesday, 06 November 2019, during the ICANN66 meeting held from 02-07 November 2019 in Montreal, Canada. The original DNSSEC Workshop has been a part of ICANN meetings for many years and has provided a forum for both experienced and new people to meet, present and discuss current and future DNSSEC deployments.
For the upcoming ICANN 66 session, the program committee added a new focus on security to the workshop to address various emerging security related issues such as DNS-over-TLS (DoT) / DNS-over-HTTPS(DoH) impacts and potential abuses, impacts of RPKI deployments, BGP hijacking and other Internet related routing issues.
For reference, the most recent session was held at the ICANN Policy Forum in Marrakech, Morocco on 24 June 2019. The presentations and transcripts are available at: https://65.schedule.icann.org/meetings/1058207 and https://65.schedule.icann.org/meetings/1058208.
The DNSSEC and Security Workshop Program Committee is developing a 3-hour program. Proposals are sought for the following topic areas:
1. Global DNSSEC Activities Panel
For this panel, we are seeking participation from those who have been involved in DNSSEC deployment as well as from those who have not deployed DNSSEC but who have a keen interest in the challenges and benefits of deployment, including Root Key Signing Key (KSK) Rollover activities and plans.
2. DNSSEC Best Practice
Now that DNSSEC has become an operational norm for many registries, registrars, and ISPs, what have we learned about how we manage DNSSEC? Do you still submit/accept DS records with Digest Type 1? What is the best practice around key roll-overs? What about Algorithm roll-overs? Do you use and support DNSKEY Algorithms 13-16? How often do you review your disaster recovery procedures? Is there operational familiarity within your customer support teams? What operational statistics have we gathered about DNSSEC? Are there experiences being documented in the form of best practices, or something similar, for transfer of signed zones? Activities and issues related to DNSSEC in the DNS Root Zone are also desired.
3. DNSSEC Deployment Challenges
The program committee is seeking input from those that are interested in implementation of DNSSEC but have general or particular concerns with DNSSEC. In particular, we are seeking input from individuals that would be willing to participate in a panel that would discuss questions of the following nature:
- Are there any policies directly or indirectly impeding your DNSSEC deployment? (RRR model, CDS/CDNSKEY automation)
- What are your most significant concerns with DNSSEC, e.g., complexity, training, implementation, operation or something else?
- What do you expect DNSSEC to do for you and what doesn’t it do?
- What do you see as the most important trade-offs with respect to doing or not doing DNSSEC?
4. Security Panel
New to the workshop, the program committee is looking for presentations on DNS and Routing topics that could impact the security and/or stability of the internet.
- DoH and DoT implementation issues, challenges and opportunities
- RPKI adoption and implementation issues, challenges and opportunities
- BGP/routing/hijack issues, challenges and opportunities
- MANRS implementation challenges and opportunities
- Emerging threats that could impact (real or perceived) the security and/or stability of the internet
- Domain hacking/hijacking prevention, best practice and techniques
- Browser related security implementations
- DMARC Challenges, opportunities and Best Practices
- BGP Flowspec challenges, opportunities and Best Practices
In addition, we welcome suggestions for additional topics, either for inclusion in the ICANN66 workshop, or for consideration for future workshops.
If you will be at ICANN 66 in Montreal (or can get there) and are interested in participating, please send a brief (1-2 sentence) description of your proposed presentation to [email protected] by Friday, 27 September 2019
Thank you,
Andrew and Kathy
On behalf of the DNSSEC and Security Workshop Program Committee:
Mark Elkins, DNS/ZACR
Jacques Latour, .CA
Russ Mundy, Parsons
Ondrej Filip, CZ.NIC
Yoshiro Yoneya, JPRS
Fred Baker, ISC
Dan York, Internet Society
Call for Participation – DNSSEC Workshop at ICANN65, Marrakech, Morocco
Posted by mlarson in Uncategorized on May 22, 2019
The DNSSEC Deployment Initiative and the Internet Society Deploy360 Programme, in cooperation with the ICANN Security and Stability Advisory Committee (SSAC), are planning a DNSSEC Workshop during the ICANN65 meeting held from 24-27 June 2019 in Marrakech, Morocco. The DNSSEC Workshop has been a part of ICANN meetings for several years and has provided a forum for both experienced and new people to meet, present and discuss current and future DNSSEC deployments. For reference, the most recent session was held at the ICANN Community Forum in Kobe, Japan on 13 March 2019. The presentations and transcripts are available at: https://64.schedule.icann.org/meetings/961937 , https://64.schedule.icann.org/meetings/961938,and https://64.schedule.icann.org/meetings/961939.
The DNSSEC Workshop Program Committee is developing a 3-hour program. Proposals will be considered for the following topic areas and included if space permits. In addition, we welcome suggestions for additional topics either for inclusion in the ICANN65 workshop, or for consideration for future workshops.
1. DNSSEC Activities Panel (Regional and global)
For this panel, we are seeking participation from those who have been involved in DNSSEC deployment in the region and also from those who have not deployed DNSSEC but who have a keen interest in the challenges and benefits of deployment, including Root Key Signing Key (KSK) Rollover activities. Now that DNSSEC has become an operational norm for many registries, registrars, and ISPs, what have we learned about how we manage DNSSEC? What is the best practice around key rollovers? How often do you review your disaster recovery procedures? Is there operational familiarity within your customer support teams? What operational statistics have we gathered about DNSSEC? Are there experiences being documented in the form of best practices, or something similar, for transfer of signed zones?If you have a specific concern about the Root Key Rollover, or believe you have a method or solution to help address impacts, we would like to hear from you.
2. DNSSEC Deployment Challenges
The program committee is seeking input from those that are interested in implementation of DNSSEC but have general or particular concerns with DNSSEC. In particular, we are seeking input from individuals that would be willing to participate in a panel that would discuss questions of the nature:
- Are there any policies directly or indirectly impeding your DNSSEC deployment? (RRR model, CDS/CDNSKEY automation)
- What are your most significant concerns with DNSSEC, e.g., complexity, training, implementation, operation or something else?
- What do you expect DNSSEC to do for you and what doesn’t it do?
- What do you see as the most important trade-offs with respect to doing or not doing DNSSEC?
We are interested in presentations related to any aspect of DNSSEC such as zone signing, DNS response validation, applications use of DNSSEC, registry/registrar DNSSEC activities, etc.
In addition, we welcome suggestions for additional topics.
If you are interested in participating, please send a brief (1-2 sentence) description of your proposed presentation to [email protected]by **Friday, 31 May 2019**
Thank you,
Kathy and Julie
On behalf of the DNSSEC Workshop Program Committee:
Mark Elkins, DNS/ZACR
Jean Robert Hountomey, AfricaCERT
Jacques Latour, .CA
Xiaodong Lee, Chinese Academy of Sciences (CAS)
Russ Mundy, Parsons
Ondrej Filip, CZ.NIC
Yoshiro Yoneya, JPRS
Dan York, Internet Society
Is my web site being used via a DNSSEC-validator?
Posted by Mark Feldman in Uncategorized on July 30, 2012
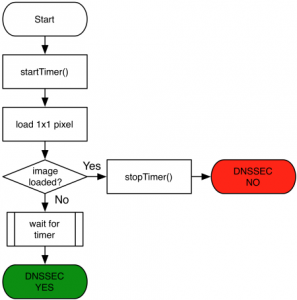 In the past, we’ve described how the graphic at the top of the DNSSEC Deployment web site let you know if you’re validating or not.
In the past, we’ve described how the graphic at the top of the DNSSEC Deployment web site let you know if you’re validating or not.
Now, Jan-Piet Mens has posted an article on how he implemented this for his web site and how you can replicate his work with his code. Thanks, Jan-Piet!
What’s *not* Changed in a Year
Posted by Ed Lewis in Uncategorized on June 20, 2012
A minor (personal) milestone — I’ve collected DNSSEC data for the root and TLDs for 366 days (1 year because of the leap day). During the collection I’ve done periodic analysis to see how DNSSEC is being driven by experts and have given a number of presentations on what’s been happening. How DNSSEC is being run? How do the operations differ from what the protocol engineers and RFC writers forecasted? There are presentations in the archives for APRICOT, ICANN, IEPG, RIPE and CENTR meetings that have been held this past winter and spring that cover these questions from different angles.
Now, at the one year mark, for fun, a look at what’s not changed.
Not so noteworthy, because KSK’s are expected to be used on the order of years, these records have been a constant:
- 70 DNSKEY records holding SEP/KSK’s
- 44 DNSKEY RRSIG records, usually signed by SEP/KSK’s
- 46 DS records in the root
But these fairly noteworthy:
- 6 RRSIG records for NSEC/NSEC3PARAM and SOA
- 9 DNSKEY records holding ZSK’s (not alarming, but…)
- 40 NSEC3PARAM – specifically 40 unchanged salts
First an explanation is needed (as usual when analyzing any set of data) – when I write that an RRSIG is unchanged, that refers to the signed-by fields and not the signature payload itself. The TLDs are refreshing signatures as needed, but when the key isn’t changed (as well as some other parameters) my analysis considers the RRSIG to be the same.
What this analysis says is that there are 6 TLDs that have used a ZSK for a full year to generate signatures. Each of the 6 keys is RSA-SHA1 and 1024 bits long. So some are challenging the (“CW”) notion that long lived keys will break. Publishing a ZSK for a year (per se) is not risky, but it shows that at least 9 ZSK’s have a longer lifetime that expected.
Besides the 6 ZSK keys that signed every day, the other three, two never generated signatures and one did so over about a 9 month period.
The 40 unchanged NSEC3PARAM records indicate that 40 TLDs have run NSEC3 for a year (plus) and have not changed the salt (as opposed to the 4 TLDs that change the salt daily or nearly daily). The RFC recommends “with every signing” but few do “batch” signing anymore.
Final note – these counts do not cover the TLDs that have begun operations within the past 366 days.
Ed Lewis
Director, Member of Technical Staff at Neustar
DNSSEC at the Pub
Posted by Mark Feldman in Uncategorized on June 18, 2012
As seen on the DNSSEC Deployment Working Group email list:
Invitation to Informal Gathering of DNSSEC Implementers in Prague 26 June
On behalf of the DNSSEC Deployment Initiative and CZ.NIC, DNSSEC Implementers are invited to attend an informal gathering to discuss and exchange information on their DNSSEC implementation experiences during the ICANN meeting in Prague, Czech Republic. This is a unique opportunity to meet with and talk to key implementers, such as CZ.NIC, Nominet UK, ISC, IIS Sweden, and others. We do ask that in order to participate you should come prepared to say a few words about your experiences. This is a peer-to-peer event for implementers.
Where: Pivovarsky klub
When: Tuesday, 26 June 2012, 6:00 to 8:00 pm
Note that this event is in addition to the other DNSSEC events scheduled during the ICANN meeting. These are:
Monday, 25 June: 4:00-5:30 pm — DNSSEC for Everybody – Roma, Details: http://prague44.icann.org/node/31657
Wednesday, 27 June: 8:30 am to 1:45 pm — DNSSEC Workshop at ICANN Meeting – Congress I, Details: http://prague44.icann.org/node/31749
**Please RSVP to [email protected] no later than Friday, 22 June if you would like to attend.**
Best regards,
Julie Hedlund
On behalf of Ondřej Surý, CZ.NIC and Steve Crocker and Russ Mundy for the DNSSEC Deployment Initiative
DNSSEC Workshop at ICANN 44
Posted by Mark Feldman in Uncategorized on June 6, 2012
 As with other recent ICANN meetings, there will be a DNSSEC workshop at ICANN 44. The workshop will be held on Wednesday, 27 June 2012 from 08:30 until 13:45 CEST (UTC/GMT +2 hours). Remote participation is available for the meeting.
As with other recent ICANN meetings, there will be a DNSSEC workshop at ICANN 44. The workshop will be held on Wednesday, 27 June 2012 from 08:30 until 13:45 CEST (UTC/GMT +2 hours). Remote participation is available for the meeting.
The agenda for the meeting as it currently stands:
1. Introduction and Presentation: DNSSEC Deployment Around the World: Steve Crocker, Shinkuro
2. DNSSEC activities in Europe
3. ISPs and Validation
4. The realities of running DNSSEC
5. DNSSEC and Enterprise Activities
6. DANE and other DNSSEC applications
7. The Great DNSSEC Panel Quiz
The Legend of DNSSEC
Posted by Mark Feldman in Uncategorized on June 5, 2012
We’ve taken to putting up animated maps of DNSSEC adoption in country code TLDs (ccTLDs) every few months (6 March 2012, 4 June 2012). One question we get is, “So, what does the legend in the maps we produce indicate?” From the past through the date of the map, the following are from observation. For dates beyond the date of the map, the following are either an extension of the observation or based on stated plans.
- Experimental (yellow) — We have reason to believe that the ccTLD is (or will be) experimenting with DNSSEC.
- Announced (orange) — The ccTLD has announced that they will support DNSSEC.
- Partial (green) — The ccTLD has signed their zone, but has not yet passed DS records up to the root and may or may not be accepting signed delegations.
- DS in Root (blue) — The ccTLS is signed and DS records for its KSKs are (or will be) in the root zone, but it is not yet accepting signed delegations.
- Operational (red) — The ccTLD is signed, it has DS records in the root, and it is accepting signed delegations (DS records from child zones).
We can and do identify current Partial and DS in Root statuses programatically. Everything else needs human input. Specifically, your input sent to info @ dnssec-deployment.org.

Recent Comments