
DNSSEC in ccTLDs, Past, Present, and Future
Posted by Mark Feldman in DNSSEC Deployment Maps on July 30, 2013
DNSSEC continues to be deployed in ccTLDs. The animation below shows the history of DNSSEC adoption through today with predictions based on announcements and other communications going forward. A high-resolution map of current deployment status is available here.
Call for Participation — ICANN DNSSEC Workshop 17 July 2013
Posted by Mark Feldman in ICANN DNSSEC Workshops, Meetings and Workshops on June 3, 2013
The DNSSEC Deployment Initiative, in cooperation with the ICANN Security
and Stability Advisory Committee (SSAC), is planning a DNSSEC Workshop at
the ICANN meeting in Durban, South Africa on 17 July 2013. The DNSSEC
Workshop has been a part of ICANN meetings for several years and has
provided a forum for both experienced and new people to meet, present and
discuss current and future DNSSEC deployments. For reference, the most
recent session was held at the ICANN meeting in Beijing, China on 10 April
2013. The presentations and transcripts are available
at http://beijing46.icann.org/node/37125.
We are seeking presentations on the following topics:
1. DNSSEC Activities in Africa
For this panel we are seeking participation from those who have been
involved in DNSSEC deployment in Africa as well as those who have a keen
interest in the challenges and benefits of deployment. Key questions are
to consider include: What would help to promote DNSSEC deployment? What
are the challenges you have faced when you deployed DNSSEC?
2. The Operational Realities of Running DNSSEC
Now that DNSSEC has become an operational norm for many registries,
registrars, and ISPs, what have we learned about how we manage DNSSEC?
What’s best practice around key rollovers? How often do you review your
disaster recovery procedures? Is there operational familiarity within your
customer support teams? Has DNSSEC made DNS more ‘brittle’ or is it just a
run-of-the-mill operational practice? What operational statistics have we
gathered about DNSSEC? Is it changing DNS patterns? How are our
nameservers handling DNSSEC traffic? Is the volume as expected? Have we
seen anything unusual? Are there experiences being documented in the form
of best practices, or something similar, for transfer of signed zones?
3. DNSSEC and Enterprise Activities
DNSSEC has always been seen as a huge benefit to organizations looking to
protect their identity and security on the Web. Large enterprises are an
obvious target for DNS hackers and DNSSEC provides an ideal solution to
this challenge. This session aims to look at the benefits and challenges
of deploying DNSSEC for major enterprises. Topics for discussion:
* What is the current status of DNSSEC deployment among enterprises?
* What plans do the major enterprises have for their DNSSEC roadmaps?
* What are the challenges to deployment for these organizations? Do they
foresee raising awareness of DNSSEC with their customers?
4. When Unexpected DNSSEC Events Occur
What have we learned from some of the operational outages that we have
seen over the past 18 months? Are there lessons that we can pass on to
those just about to implement DNSSEC? How do you manage dissemination of
information about the outage? What have you learned about communications
planning? Do you have a route to ISPs and registrars? How do you liaise
with your CERT community?
5. Preparing for Root Key Rollover
For this topic we are seeking input on issues relating to root key
rollover. In particular, we are seeking comments from vendors, ISPs, and
the community that will be affected by distribution of new root keys.
6. DNSSEC: Regulative, Legislative and Persuasive Approaches to
Encouraging Deployment
There are many models in discussion for encouraging the take-up of DNSSEC
amongst TLDs. In some jurisdictions we have seen governmental edicts
insisting that DNSSEC is deployed across a Top Level Domain. In others, we
have seen reports produced for governments highlighting the lack of take
up and the need for tighter control amongst operators. Recently, we have
witnessed the consideration of mandated DNSSEC signing of zones by some
TLDs in order to gain access to newer premium domains. Have any of these
approaches worked in encouraging take up of DNSSEC? What role does a
national government have in assisting deployment of DNSSEC? How are some
of these measures perceived by registrars, DNS operators, ISPs and
registrants?
7. DANE and Other DNSSEC Applications
Using DNSSEC as a means of authentication for http transactions is an
exciting development of DNSSEC. What is the progress of the DNS-Based
Authentication of Named Entities (DANE) initiative? (See
http://datatracker.ietf.org/wg/dane/.) How soon could DANE become a
deployable reality and what will be the impact of such a deployment, e.g.
impact on traditional certification authorities (CAs)?
8. Use of DNSSEC in the Reverse Space
This topic includes signed reverse zones, security products using reverse
DNS lookup for DNSSEC validation?
9. The Great DNS Panel Quiz
Ever fancied pitting your wits against your colleagues? Demonstrate your
knowledge and expertise in DNSSEC in our Great DNSSEC Panel Quiz.
In addition, we welcome suggestions for additional topics.
If you are interested in participating, please send a brief (1-2 sentence)
description of your proposed presentation to [email protected] by
**Monday, 10 June.**
We hope that you can join us.
Thank you,
Julie Hedlund
On behalf of the DNSSEC Workshop Program Committee:
Steve Crocker, Shinkuro
Mark Elkins, DNS/ZACR
Cath Goulding, Nominet UK
Jean Robert Hountomey, AfricaCERT
Jacques Latour, .CA
Xiaodong Lee, CNNIC
Russ Mundy, Sparta/Parsons
Ondřej Surý, CZ.NIC
Lance Wolak, .ORG, The Public Interest Registry
Yoshiro Yoneya, JPRS
Dan York, Internet Society
Invitation to Informal Gathering of DNSSEC Implementers in Beijing, China, 08 April 2013
Posted by Mark Feldman in ICANN DNSSEC Workshops on April 2, 2013
** Please RSVP to [email protected] no later than Thursday, 04 April if you would like to attend.**
DNSSEC Roadmap
Posted by Mark Feldman in About The DNSSEC Deployment Initiative on March 18, 2013
The DNSSEC Roadmap, prepared in February 2013 for the Department of Homeland Security’s DNSSEC Deployment Initiative, lays out a vision for where the Initiative should go and describes next steps that various actors should take to realize a world in which every zone is signed and every query is checked. It describes the state of the art of DNSSEC deployment in the U.S. and beyond, and includes pointers toward tools, technologies and strategies that both public and private-sector groups can use to increase that deployment.
Signed Root Deployment: Framing the Issues
Posted by Mark Feldman in DNSSEC on March 18, 2013
This report, written in 2009 following the inaugural symposium of the DNSSEC Industry Coalition but unpublished until now, covers issues that remain important to ongoing DNSSEC deployment efforts. Written before the signing of the root zone, the “avoiding unintended consequences” section has been superseded by events, but the discussions of key distribution and use and key rollover remain as critical as ever for DNS and DNSSEC practitioners. [Note that this PDF contains comment markup from symposium participants.]
How Well Do Your Resolvers Support DNSSEC?
Posted by Wes Hardaker in Adoption on March 7, 2013
You probably use multiple DNS resolvers on multiple devices through the course of the day, as you wander to and from home, work, coffee shops, etc. Your desktop uses them. Your laptop uses them. Even your cellphone and tablets use them. But how well prepared are all of these resolvers for DNSSEC? Can they assist your applications in determining which DNS records have been secured or not?
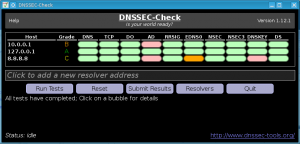
By using the DNSSEC-Check tool from the DNSSEC-Tools project, you can find out! This handy utility will test your neighboring resolvers, and any additional ones you provide it, for their support of critical DNSSEC required protocol features. After testing is done, it will even provide you with a letter grade for each resolver. Ideally, every resolver should have an A grade (indicating that not only does it support DNSSEC queries, but is a DNSSEC validating resolver itself). But if not, the colored bubbles will quickly let you know exactly which features a resolver might be missing to be fully DNSSEC compliant.
Additionally, the DNSSEC-Check utility lets you submit your anonymized results to a results collection server. These collected results let the DNSSEC-Tools project track the state of world deployment over time. So, once you find out your local resolvers are not “quite up to the task”, then you can keep checking over time to see if they’ve been updated (or better yet, update them yourself if you can!). Then resubmit the results once things have changed! The results of this collection engine can be found on the DNSSEC-Check Results page. Submitting data is entirely optional, so thanks in advance if you are willing to help us out!
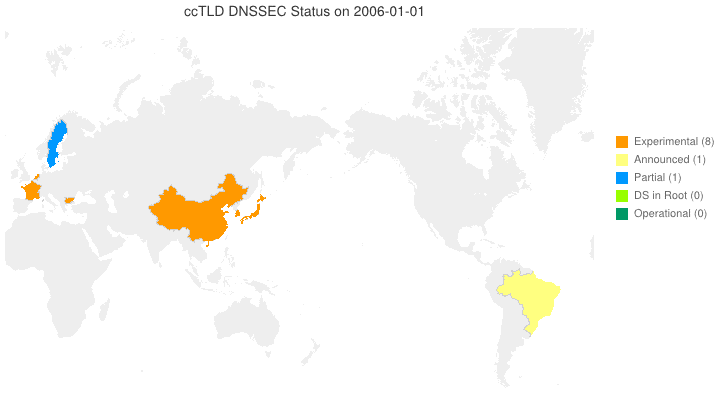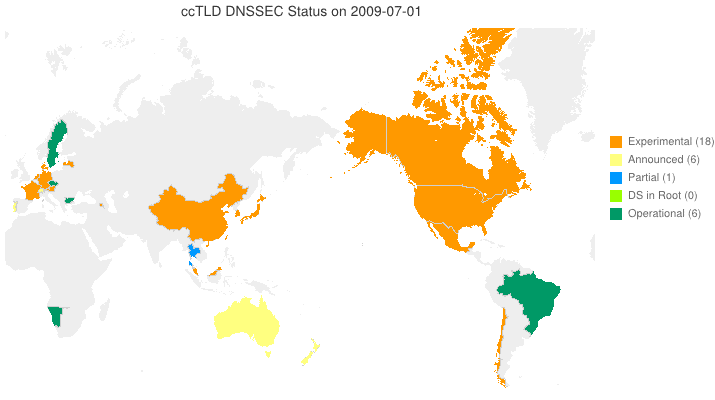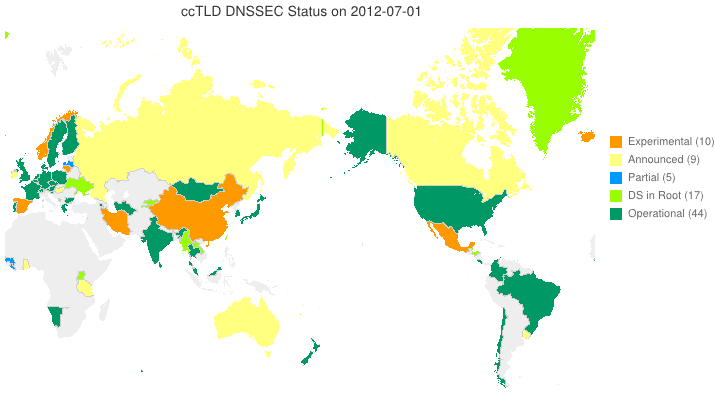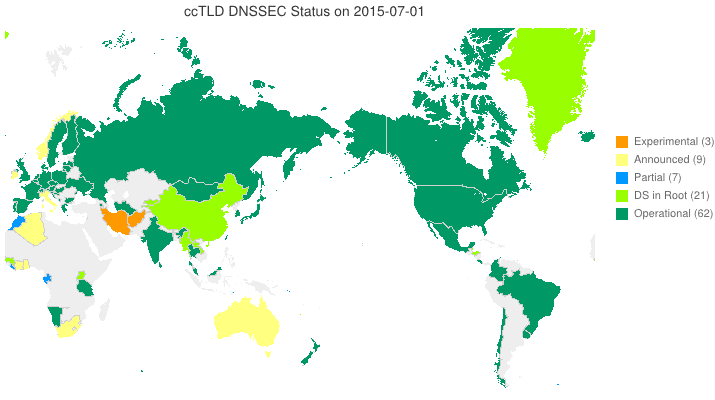
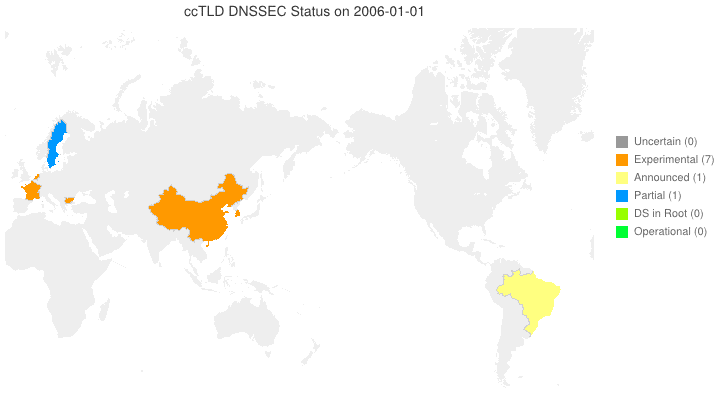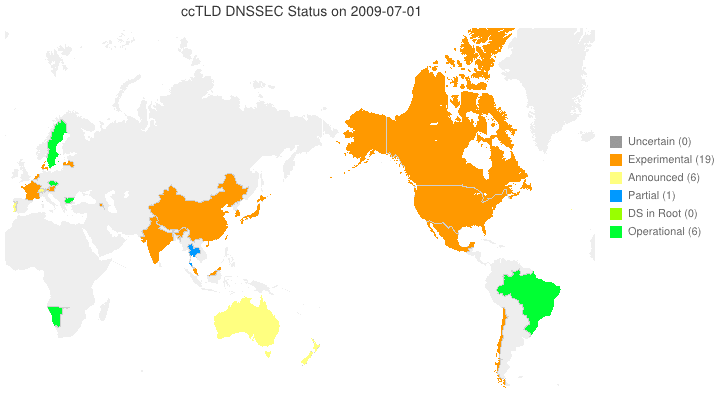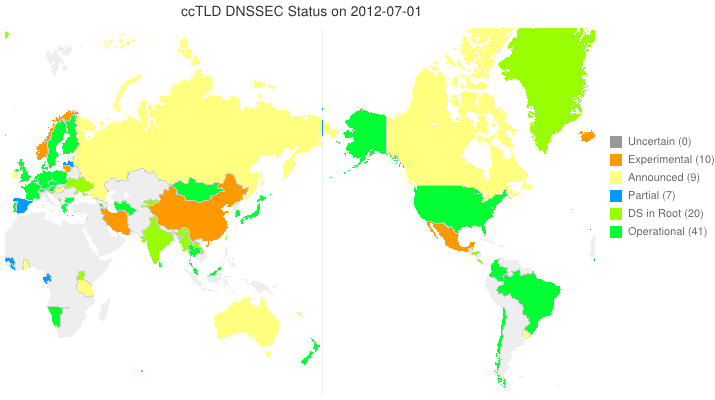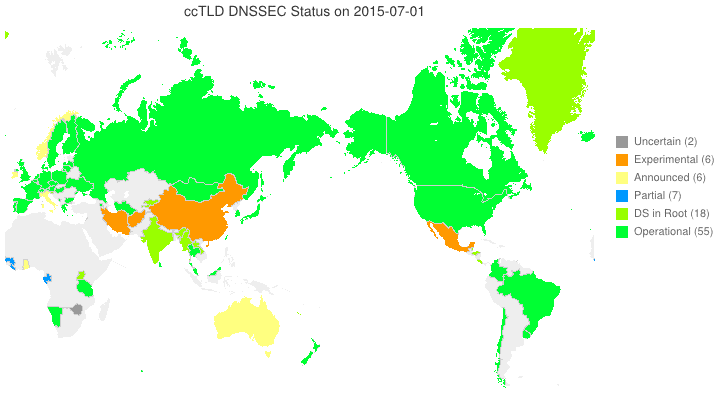
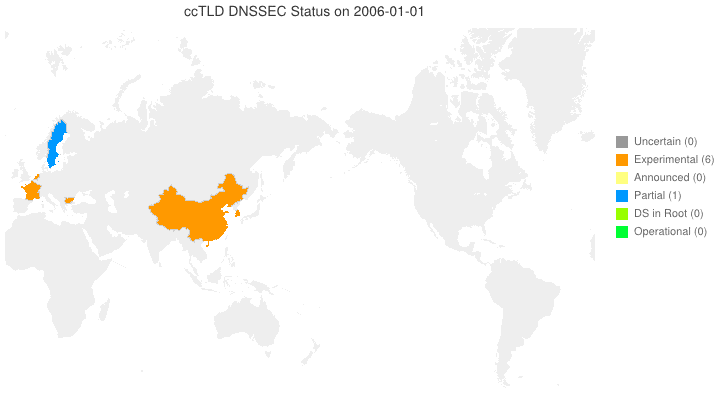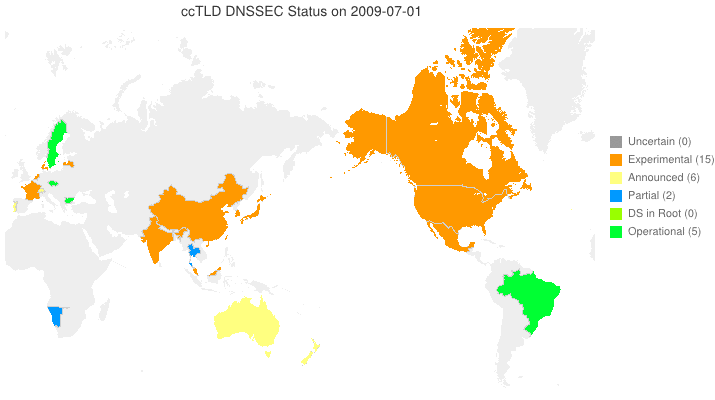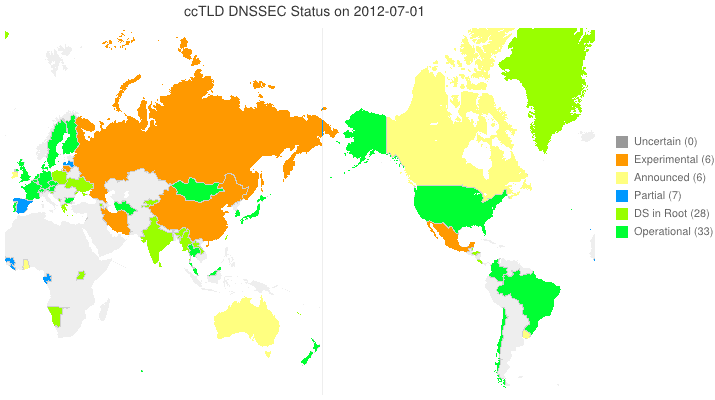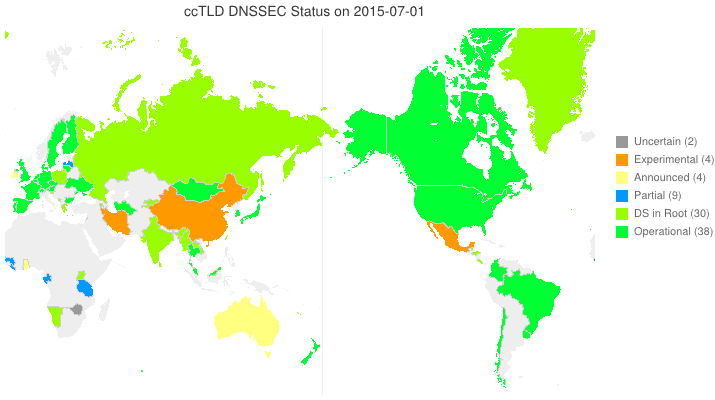
DNSSEC in ccTLDs, Past, Present, and Future
Posted by Mark Feldman in DNSSEC Deployment Maps on February 19, 2013
We sent a survey to ccTLD administrators about their adoption of DNSSEC. Below is a new animated map based on the initial flurry of responses we received. Many zones which we knew from observation to have their DS in the root turn out to be accepting delegations and are, therefore, fully operational! A high resolution PDF map is available here.
DNSSEC in ccTLDs, Past, Present, and Future
Posted by Mark Feldman in DNSSEC Deployment Maps on February 1, 2013
This animated GIF shows announced, estimated, and actual DNSSEC adoption by ccTLDs from January 2006 through July 2015 as of 1 February 2013. We’d like to see a more colorful, even completely green, map in the future. We also have a high-resolution PDF map of the world with ccTLD DNSSEC adoption as of 1 February 2013 here.
The maps are a work in progress. We’re pretty sure about the past and present. If you manage a ccTLD and have a schedule for deployment or have updates/corrections, let us know at info @ dnssec-deployment.org.
DNS Cache Poisoning Attack in Romania – Popular Sites Redirected.
Posted by Scott Rose in DNSSEC, News on December 3, 2012
Arstechnica reports that a possible DNS cache poisoning attack was used against the Romanian (.ro) versions of popular sites like Google, PayPal and Microsoft. While the exact cause is unknown, cache poisoning is suspected since it involved multiple domain names, but not the whole of the .ro domain:
For a span of one to several hours on Wednesday morning, people typing Google.ro, Yahoo.ro, and Romanian-specific addresses for other sites connected to a website that was purportedly run by an Algerian hacker, according to numerous security blog posts, including this one from Kaspersky Lab. Researchers said the most likely explanation for the redirection is a technique known as DNS poisoning, in which domain name system routing tables are tampered with, causing domain names to resolve to incorrect IP addresses.
More information from Kaspersky Lab.
Is my web site being used via a DNSSEC-validator?
Posted by Mark Feldman in Uncategorized on July 30, 2012
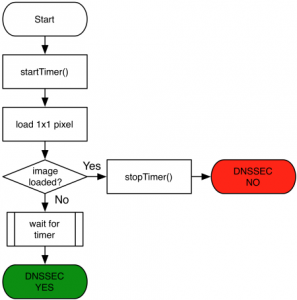 In the past, we’ve described how the graphic at the top of the DNSSEC Deployment web site let you know if you’re validating or not.
In the past, we’ve described how the graphic at the top of the DNSSEC Deployment web site let you know if you’re validating or not.
Now, Jan-Piet Mens has posted an article on how he implemented this for his web site and how you can replicate his work with his code. Thanks, Jan-Piet!

Recent Comments