
Archive for March, 2013
DNSSEC Roadmap
Posted by Mark Feldman in About The DNSSEC Deployment Initiative on March 18, 2013
The DNSSEC Roadmap, prepared in February 2013 for the Department of Homeland Security’s DNSSEC Deployment Initiative, lays out a vision for where the Initiative should go and describes next steps that various actors should take to realize a world in which every zone is signed and every query is checked. It describes the state of the art of DNSSEC deployment in the U.S. and beyond, and includes pointers toward tools, technologies and strategies that both public and private-sector groups can use to increase that deployment.
Signed Root Deployment: Framing the Issues
Posted by Mark Feldman in DNSSEC on March 18, 2013
This report, written in 2009 following the inaugural symposium of the DNSSEC Industry Coalition but unpublished until now, covers issues that remain important to ongoing DNSSEC deployment efforts. Written before the signing of the root zone, the “avoiding unintended consequences” section has been superseded by events, but the discussions of key distribution and use and key rollover remain as critical as ever for DNS and DNSSEC practitioners. [Note that this PDF contains comment markup from symposium participants.]
How Well Do Your Resolvers Support DNSSEC?
Posted by Wes Hardaker in Adoption on March 7, 2013
You probably use multiple DNS resolvers on multiple devices through the course of the day, as you wander to and from home, work, coffee shops, etc. Your desktop uses them. Your laptop uses them. Even your cellphone and tablets use them. But how well prepared are all of these resolvers for DNSSEC? Can they assist your applications in determining which DNS records have been secured or not?
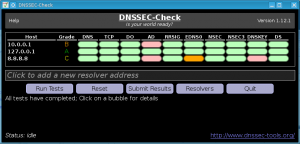
By using the DNSSEC-Check tool from the DNSSEC-Tools project, you can find out! This handy utility will test your neighboring resolvers, and any additional ones you provide it, for their support of critical DNSSEC required protocol features. After testing is done, it will even provide you with a letter grade for each resolver. Ideally, every resolver should have an A grade (indicating that not only does it support DNSSEC queries, but is a DNSSEC validating resolver itself). But if not, the colored bubbles will quickly let you know exactly which features a resolver might be missing to be fully DNSSEC compliant.
Additionally, the DNSSEC-Check utility lets you submit your anonymized results to a results collection server. These collected results let the DNSSEC-Tools project track the state of world deployment over time. So, once you find out your local resolvers are not “quite up to the task”, then you can keep checking over time to see if they’ve been updated (or better yet, update them yourself if you can!). Then resubmit the results once things have changed! The results of this collection engine can be found on the DNSSEC-Check Results page. Submitting data is entirely optional, so thanks in advance if you are willing to help us out!

Recent Comments