Archive for June, 2012
Authenticated Denial of Existence
Posted by Mark Feldman in News, Tools on June 28, 2012
 Effective immediately, this site will be renamed The .NL Gazette. Well, maybe not, but the folks at SIDN, the .NL registry, just keep producing good stuff.
Effective immediately, this site will be renamed The .NL Gazette. Well, maybe not, but the folks at SIDN, the .NL registry, just keep producing good stuff.
We’ve recently reported on their becoming DNSSEC operational and their surpassing .COM in the number of signed zones. A couple of months back we lauded their excellent DNSSEC tutorial. We’ve also mentioned several of the tools they’ve NLNet Labs produced (NSD, Unbound, Dnssec-Trigger) when talking about labs and in our articles on adding DNSSEC validation to a $70 router and its performance.
[Correction 3 July 2012: Why the strikeout above? Olaf M. Kolkman of NLNet Labs points out that while SIDN and NLNet Labs have had a collaborative agreement since the beginning of this year, NSD, Unbound, and Dnssec-Trigger are products of NLNet Labs. We’re just happy that both SIDN and NLNet Labs are helping advance DNSSEC and don’t for one second want to confuse the two just because they’re both in The Netherlands! To further make things clear, neither SIDN nor NLNet Labs produce Koetjesreep, so don’t ask for a few bars. Thanks for the correction, Olaf!]
Now it’s time to let people know about one of their more technical articles,
Authenticated Denial of Existence in the DNS (277KB PDF). We ran across it while trying to debug some validation software.
The article tells the story behind why negative responses must be signed and how they can state with security and certainty that a name/resource record type combination does not exist. The article augments RFCs 4033, 4034, 4035, and 5155.
It provides the kinds of additional information in narrative and graphic format that helps with understanding. If you want to now how authenticated denial of existence works, check out the article.
.nl passeert .com met DNSSEC
Posted by Mark Feldman in News on June 27, 2012
Webwereld’s story about DNSSEC adoption in .NL describes how, with under five million domains, .NL has almost 12,000 using DNSSEC — more than the number of DNSSEC-enabled domains in .COM.
Current counts of domain registrations and DNSSEC use for .NL are in the right-hand sidebar of SIDN’s web site (and English translation).
NIST Special Publication 800-81 Revision: Sections 1-5
Posted by Scott Rose in Technical guides on June 21, 2012
Note: This is the second post in a series about the revision of NIST Special Publication (SP) 800-81: Secure Domain Name System (DNS) Deployment Guide.
In revising NIST SP 800-81, I am going through it section by section and seeing what parts need to be revised. This is in addition to an entirely new section with recommendations on recursive servers and validators.
Looking at Sections 1-5, there seems to be relatively little that needs changing, but let’s break it down by section:
Section 1 Introduction: Besides minor updates, bring it into conformance with the newly added section(s), not much to do here.
Section 2 Securing Domain Name System: Most of this section provides background on the DNS and breaks down the various components. Again, since there haven’t been any radical changes to the DNS protocol itself, there aren’t any significant changes. Maybe some additional text in this section about new gTLDs? Other than more information, it will not add anything significant.
Section 3 DNS Data and DNS Software: This section describes the basic roles (authoritative and caching severs). Should a subsection on validators be included? Are validators different enough to include it as a separate subsection or just include some discussion in the subsection covering resolvers?
Section 4 DNS Transactions: and message types (query, dynamic update, NOTIFY, etc.). This section describes the basic transactions in DNS (i.e., query/response, etc.). Since there hasn’t been a new DNS transaction type defined since the first version of this publication, no apparent edits are needed here.
Section 5 DNS Hosting Environment – Threats, Security Objectives and Protection Approaches: This section details some threats to the host systems used in DNS (i.e., servers, resolvers). Most of the section is still relevant, but might need some updating to the sub-section on resolvers to address validation. The discussion is high-level, so trends like virtualization do not need to be discussed, but may be included if there are valid concerns.
As before, comments and/or opinions on the questions above, post them below. They will be considered as the SP 800-81 revision process continues.
The views presented here are those of the author and do not necessarily represent the views or policies of NIST.
What’s *not* Changed in a Year
Posted by Ed Lewis in Uncategorized on June 20, 2012
A minor (personal) milestone — I’ve collected DNSSEC data for the root and TLDs for 366 days (1 year because of the leap day). During the collection I’ve done periodic analysis to see how DNSSEC is being driven by experts and have given a number of presentations on what’s been happening. How DNSSEC is being run? How do the operations differ from what the protocol engineers and RFC writers forecasted? There are presentations in the archives for APRICOT, ICANN, IEPG, RIPE and CENTR meetings that have been held this past winter and spring that cover these questions from different angles.
Now, at the one year mark, for fun, a look at what’s not changed.
Not so noteworthy, because KSK’s are expected to be used on the order of years, these records have been a constant:
- 70 DNSKEY records holding SEP/KSK’s
- 44 DNSKEY RRSIG records, usually signed by SEP/KSK’s
- 46 DS records in the root
But these fairly noteworthy:
- 6 RRSIG records for NSEC/NSEC3PARAM and SOA
- 9 DNSKEY records holding ZSK’s (not alarming, but…)
- 40 NSEC3PARAM – specifically 40 unchanged salts
First an explanation is needed (as usual when analyzing any set of data) – when I write that an RRSIG is unchanged, that refers to the signed-by fields and not the signature payload itself. The TLDs are refreshing signatures as needed, but when the key isn’t changed (as well as some other parameters) my analysis considers the RRSIG to be the same.
What this analysis says is that there are 6 TLDs that have used a ZSK for a full year to generate signatures. Each of the 6 keys is RSA-SHA1 and 1024 bits long. So some are challenging the (“CW”) notion that long lived keys will break. Publishing a ZSK for a year (per se) is not risky, but it shows that at least 9 ZSK’s have a longer lifetime that expected.
Besides the 6 ZSK keys that signed every day, the other three, two never generated signatures and one did so over about a 9 month period.
The 40 unchanged NSEC3PARAM records indicate that 40 TLDs have run NSEC3 for a year (plus) and have not changed the salt (as opposed to the 4 TLDs that change the salt daily or nearly daily). The RFC recommends “with every signing” but few do “batch” signing anymore.
Final note – these counts do not cover the TLDs that have begun operations within the past 366 days.
Ed Lewis
Director, Member of Technical Staff at Neustar
DNSSEC at the Pub
Posted by Mark Feldman in Uncategorized on June 18, 2012
As seen on the DNSSEC Deployment Working Group email list:
Invitation to Informal Gathering of DNSSEC Implementers in Prague 26 June
On behalf of the DNSSEC Deployment Initiative and CZ.NIC, DNSSEC Implementers are invited to attend an informal gathering to discuss and exchange information on their DNSSEC implementation experiences during the ICANN meeting in Prague, Czech Republic. This is a unique opportunity to meet with and talk to key implementers, such as CZ.NIC, Nominet UK, ISC, IIS Sweden, and others. We do ask that in order to participate you should come prepared to say a few words about your experiences. This is a peer-to-peer event for implementers.
Where: Pivovarsky klub
When: Tuesday, 26 June 2012, 6:00 to 8:00 pm
Note that this event is in addition to the other DNSSEC events scheduled during the ICANN meeting. These are:
Monday, 25 June: 4:00-5:30 pm — DNSSEC for Everybody – Roma, Details: http://prague44.icann.org/node/31657
Wednesday, 27 June: 8:30 am to 1:45 pm — DNSSEC Workshop at ICANN Meeting – Congress I, Details: http://prague44.icann.org/node/31749
**Please RSVP to [email protected] no later than Friday, 22 June if you would like to attend.**
Best regards,
Julie Hedlund
On behalf of Ondřej Surý, CZ.NIC and Steve Crocker and Russ Mundy for the DNSSEC Deployment Initiative
New Revision of NIST Special Publication (SP) 800-81 Under Way
Posted by Scott Rose in Technical guides on June 15, 2012
This inaugural post is the first in a series documenting the update of NIST SP 800-81, Secure Domain Name System (DNS) Deployment Guide. The current version (SP 800-81r1) was published in April 2010. Since that date, DNSSEC deployment Internet-wide had matured and advanced to the point where a new revision is justified.
The goal of the new revision of NIST SP 800-81 is to incorporate updates to recommendations based on currently deployment experiences. There have also been recent developments in specification of new cryptographic algorithms for use with DNSSEC (such as Elliptic Curve). The new revision will add discussion on new crypto algorithms as well as update the existing recommendations for DNS and DNSSEC operation.
We are also planning a new section of the document to provide guidance and recommendations for recursive DNS servers and validators. With DNSSEC deployment on the rise, more enterprises (and even ISPs) are configuring DNSSEC validation. Validation is also a planned required control in the upcoming revision of FISMA (NIST SP 800-53r4), so the new sections will be timely.
The plan is to have regular updates on this blog as the draft revision progresses. This is also one of the forums to discuss the revision during the process. As with all NIST Special Publications, there will be a draft document posted with an official comment period; this blog is simply an attempt to solicit input before the initial public draft is released for public comment.
The views presented here are those of the author and do not necessarily represent the views or policies of NIST.
DNSSEC Workshop at ICANN 44
Posted by Mark Feldman in Uncategorized on June 6, 2012
 As with other recent ICANN meetings, there will be a DNSSEC workshop at ICANN 44. The workshop will be held on Wednesday, 27 June 2012 from 08:30 until 13:45 CEST (UTC/GMT +2 hours). Remote participation is available for the meeting.
As with other recent ICANN meetings, there will be a DNSSEC workshop at ICANN 44. The workshop will be held on Wednesday, 27 June 2012 from 08:30 until 13:45 CEST (UTC/GMT +2 hours). Remote participation is available for the meeting.
The agenda for the meeting as it currently stands:
1. Introduction and Presentation: DNSSEC Deployment Around the World: Steve Crocker, Shinkuro
2. DNSSEC activities in Europe
3. ISPs and Validation
4. The realities of running DNSSEC
5. DNSSEC and Enterprise Activities
6. DANE and other DNSSEC applications
7. The Great DNSSEC Panel Quiz
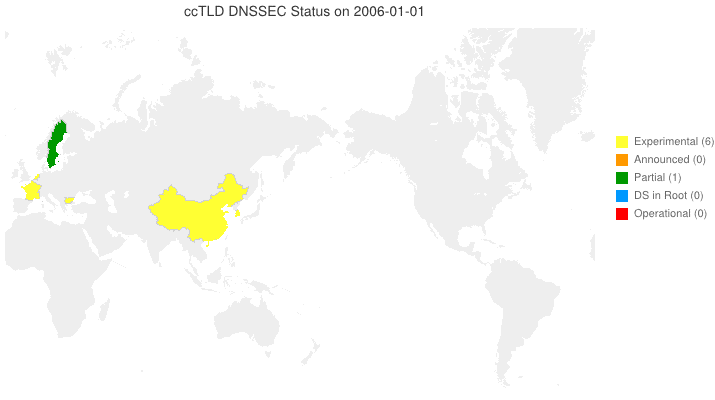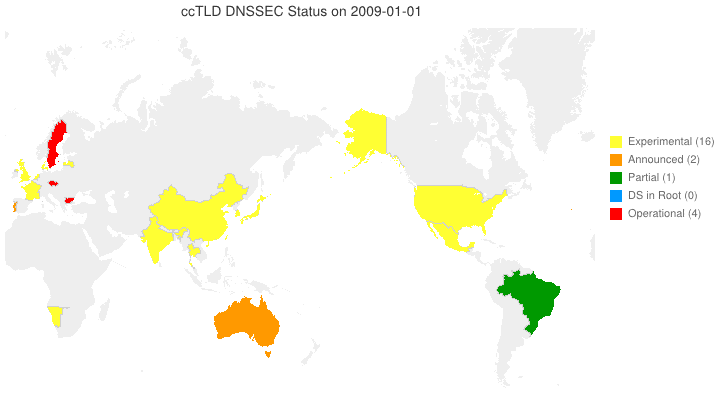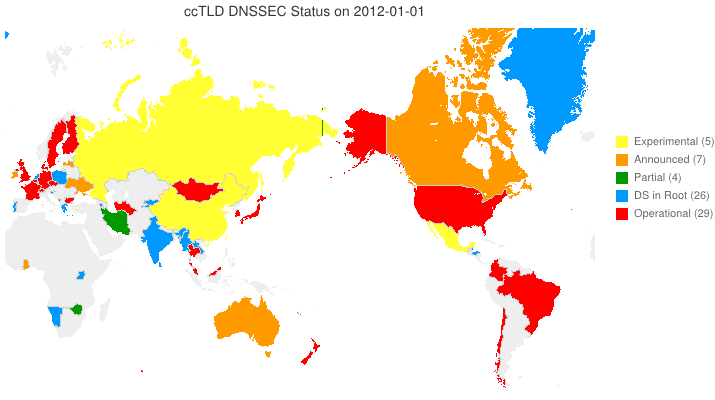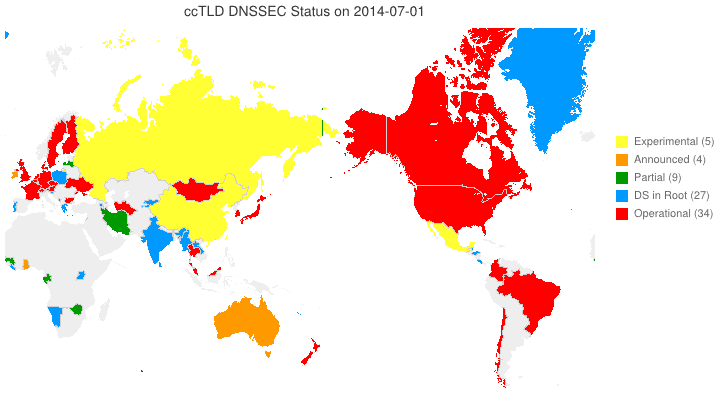
The Legend of DNSSEC
Posted by Mark Feldman in Uncategorized on June 5, 2012
We’ve taken to putting up animated maps of DNSSEC adoption in country code TLDs (ccTLDs) every few months (6 March 2012, 4 June 2012). One question we get is, “So, what does the legend in the maps we produce indicate?” From the past through the date of the map, the following are from observation. For dates beyond the date of the map, the following are either an extension of the observation or based on stated plans.
- Experimental (yellow) — We have reason to believe that the ccTLD is (or will be) experimenting with DNSSEC.
- Announced (orange) — The ccTLD has announced that they will support DNSSEC.
- Partial (green) — The ccTLD has signed their zone, but has not yet passed DS records up to the root and may or may not be accepting signed delegations.
- DS in Root (blue) — The ccTLS is signed and DS records for its KSKs are (or will be) in the root zone, but it is not yet accepting signed delegations.
- Operational (red) — The ccTLD is signed, it has DS records in the root, and it is accepting signed delegations (DS records from child zones).
We can and do identify current Partial and DS in Root statuses programatically. Everything else needs human input. Specifically, your input sent to info @ dnssec-deployment.org.
DNSSEC in ccTLDs, Past, Present, and Future
Posted by Mark Feldman in Uncategorized on June 4, 2012
This animated GIF shows announced, estimated, and actual DNSSEC adoption by ccTLDs from January 2006 through July 2014 as of 4 June 2012. The map is a work in progress. We’re pretty sure about the past and present. If you manage a ccTLD and have a schedule for deployment or have updates/corrections, let us know at info @ dnssec-deployment.org. We’d like to see a more colorful, even completely red, map in the future



Recent Comments